Iran readies anti-virus for 'Flame' spy malware
ISTANBUL- Hürriyet Daily News

Iran claimed on Tuesday to have come up with an anti-virus programme against "Flame," extraordinarily sophisticated malware that hit its servers and deployed various spying modules, apparently at the behest of a foreign power.
"Tools to recognise and clean this malware have been developed and, as of today, they will be available for those (Iranian) organisations and companies who want it," Maher, a computer emergency response team coordination centre in Iran's telecommunications ministry, said on its website.
Flame, a crafty volume of code that can steal files, take screenshots, activate computer microphones to record conversations, log keystrokes and carry out other activities controlled remotely, was identified this week by leading anti-virus firms around the world.
Maher said Flame was undetectable by 43 different anti-virus programmes it tested, forcing it to come up with its own defence after "months of research." It did not give details of how its Flame-killer worked.
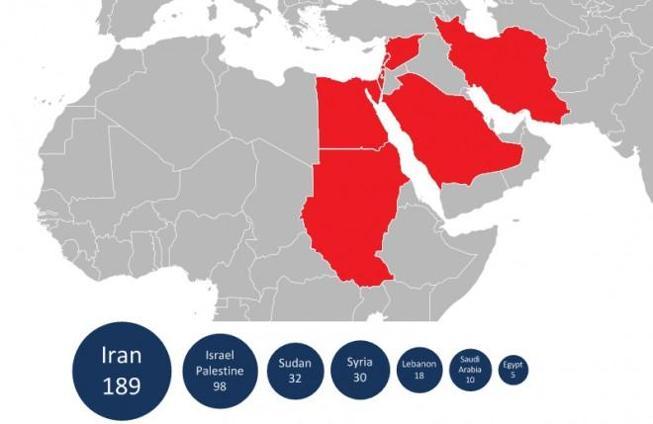
Iran appeared to be the main target of the worm-like malware, though it was also detected in other regions, including Israel and the Palestinian Territories, Sudan and Syria.
The virus hit Iran's oil ministry servers in April, forcing authorities to shut them down.
"Experts from Maher... have said that the theft of large volumes of data in recent weeks was caused by Flame," the Fars news agency reported.
Iran's foreign ministry spokesman, Ramin Mehmanparast, hinted that Israel could be behind the attack.
"It's in the nature of some countries or illegitimate regimes to produce viruses and hurt other countries. We hope that these viruses are knocked out and no one gets hurt," he told reporters in his weekly briefing.

Map showing the number and geographical location of Flame infections detected by Kaspersky Lab on customer machines.
Courtesy of KasperskyUse of Flame virus to deter Iran 'reasonable': Israel
For anyone facing the threat of a nuclear Iran, using cyberweapons such as the newly-discovered destructive virus known as Flame, would be a "reasonable" step, Israel's vice prime minister said on Tuesday.
"For anyone who sees the Iranian threat as significant, it is reasonable that he would take different steps, including these, in order to damage it," Strategic Affairs Minister Moshe Yaalon told Israel's army radio on Tuesday, just hours after the virus was discovered by Kaspersky Lab.
"Israel is blessed with being a country which is technologically rich, and these tools open up all sorts of possibilities for us," he said.
Late on Monday, Kaspersky Labs, a top Russian anti-virus firm said it had uncovered a new virus with unprecedented destructive potential, which was being used as a "cyberweapon" against several countries.
Kaspersky said the virus was several times larger than the Stuxnet worm that was discovered in June 2010 and used against the Iranian nuclear programme, with Israel widely suspected of involvement along with Western security agencies.
Flame is "actively being used as a cyber weapon attacking entities in several countries," a Kaspersky statement said, describing its purpose as "cyberespionage."
20 times larger than Stuxnet "The complexity and functionality of the newly discovered malicious programme exceed those of all other cyber menaces known to date," it added.
It did not mention which country the virus was aimed at, but said the investigation began following complaints from the U.N.'s International Telecommunication Union about a piece of malware named Wiper, which was deleting sensitive information across the Middle East.
The malware code itself is 20MB in size - making it some 20 times larger than the Stuxnet virus.
According to Western media reports, Flame has been used to attack the Iranian oil ministry and Iran's main oil export terminal.
Kaspersky said Flame had been "in the wild" for more than two years, since March 2010. Officials with Symantec Corp and Intel Corp McAfee security division, the top 2 makers of anti-virus software, said they were studying Flame.
"It seems to be more complex than Duqu but it's too early to tell its place in history," said Dave Marcus, director of advanced research and threat intelligence with McAfee.
Most complex malicious softwareSymantec Security Response manager Vikram Thakur said his company's experts believed there was a "high" probability that Flame was among the most complex pieces of malicious software ever discovered.
There is some controversy over who was behind Stuxnet and Duqu. Some experts suspect the United States and Israel, a view laid out in a January 2011 New York Times report that said they came from a joint program begun around 2004 to undermine what they said were Iran's efforts to build a bomb.
The U.S. Defense Department, CIA, State Department, National Security Agency, and U.S. Cyber Command declined to comment.
Hungarian researcher Boldizsar Bencsath, whose Laboratory of Cryptography and Systems Security first discovered Duqu, said his analysis showed that Flame may have been active for at least five years, perhaps even more than eight years.
That implies it was active long before Stuxnet.
"It's huge and overly complex, which makes me think it's a first-generation data gathering tool," said Neil Fisher, vice president for global security solutions at Unisys Corp. "We are going to find more of these things over time."
Prof Alan Woodward, from the Department of Computing at the University of Surrey said the attack was very significant. "This is basically an industrial vacuum cleaner for sensitive information," he told the BBC. He explained that unlike Stuxnet, which was designed with one specific task in mind, Flame was much more sophisticated. "Whereas Stuxnet just had one purpose in life, Flame is a toolkit, so they can go after just about everything they can get their hands on."
Once the initial Flame malware has infected a machine, additional modules can be added to perform specific tasks - almost in the same manner as adding apps to a smartphone.
Compiled from AFP, Reuters and BBC stories by the Daily News staff.
 Iran claimed on Tuesday to have come up with an anti-virus programme against "Flame," extraordinarily sophisticated malware that hit its servers and deployed various spying modules, apparently at the behest of a foreign power.
Iran claimed on Tuesday to have come up with an anti-virus programme against "Flame," extraordinarily sophisticated malware that hit its servers and deployed various spying modules, apparently at the behest of a foreign power.